Security Services
Cyber Security is vast subject and there are number of services to offer. We cover complete cyber security services. Below are some offerings we have, however not limited to.
Vulnerability Assessment and Penetration Testing (VAPT)
Usage of best industry practices and blending the same with emerging technologies to identify and address product/platform related security vulnerabilities in advance. Security is the main concern of the organizations these days. The cyber-crimes are on the rise and are penalizing different organizations at a very rapid pace, in case if they don’t have an efficient security system which could save them. These attacks and threats require just an opening which could help them sneak in and start their damage.
Area of Specialization
Web Applications
Mobile Platforms (Android and IoS)
Cloud Architecture (AWS)
Web Servers
Value Propositions
Hacker proof websites
Prevention of data theft
Prevention of fiscal loss
Online reputation management
Customer empowerment
Optimizing ROI
Computer Forensics
There’s been a significant rise in the amount of computer and internet related crime in recent years. This is hardly surprising as we increasingly rely on computers and the internet to carry out transactions and store and exchange information. The very nature of computers means that whatever you do leaves a trail of evidence, but in order to be used in court this needs to be gathered and handled in such a way that it isn’t compromised. This is where digital forensics comes into play.
Though the gathering of digital evidence now plays a key part in the investigation of many crimes, it’s also used by a growing number of businesses. The skills of a computer investigator can be useful in uncovering misuse of company computers or email, or the copying and leaking of data from within an organization. Our services can of course be adapted to meet the specific needs of the client.
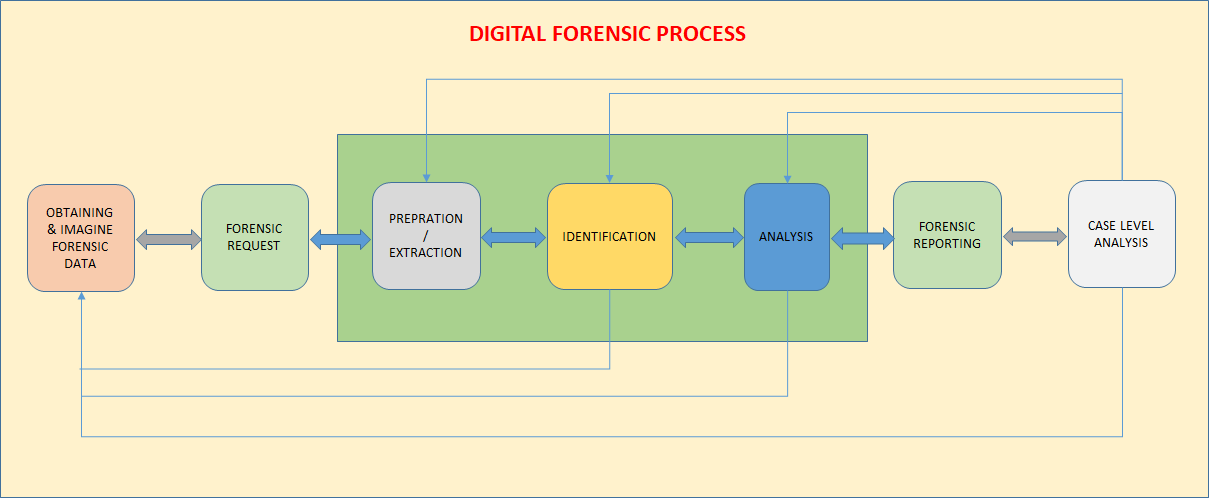
Our Approach
Evidence Assessment
Evidence Acquisition
Evidence Examination
Policy and Procedure Development
Documenting and Reporting
Types of Forensic Investigation
Workplace and Fraud Investigation
Intellectual Property Theft
Computer Hacking Investigations
Authentication of Files
Mobile Technology
Recovering Data
eDiscovery
Tracing Email
Internet Investigation
Incident Response and Malware Assessment
Incident response is the methodology an organization uses to respond to and manage a cyberattack. An attack or data breach can wreak havoc potentially affecting customers, intellectual property company time and resources, and brand value. We offer peace of mind in the face of modern cyber threats through our services and expertise in cyber security domain by minimizing the impact of a cyber attack.
Malware Analysis Service helps protect your business from all types of malware attacks online. We have expertise in malware analysis and reverse engineering supports our research, incident response, and product development. With extensive experience in reverse engineering and malicious code analysis. They have a deep practical and theoretical understanding of tools and tradecraft from across the industry.
Our Approach
Preparation
Identification
Containment
Eradication
Recovery
Lessons Learned
Value Propositions
Lower Investigative Costs
Targeted Security Monitoring
Fast Disclosure & Penalty Avoidance
Investor Confidence
Enhanced eDiscovery
Crime Deterrence
Cyber Risk Insurance
A cyber risk insurance program helps an organization mitigate the financial loss to a business due to a risk of data breach exposure. Cyber Liability insurance covers direct loss, legal liability, and consequential loss resulting from cyber security breaches. Cyber Liability insurance allows companies to focus on rebuilding and restoring their customers’ confidence without worrying about the data breach-related expenses.
Coverage
The basis of any cyber risk insurance program is the cover for third-party liabilities – legal or regulatory actions, and first-party costs associated with the response to the data breach. First-party coverage can help cover expenses when your network is hacked and data breached. Third-party coverage offers protection when a customer or a third-party file a lawsuit for al-lowing a data breach on your network.
